We have got this message below when trying to connect via SSH, WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED
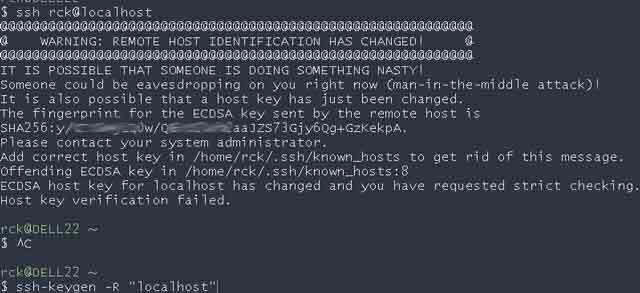
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ @ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @ @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY! Someone could be eavesdropping on you right now (man-in-the-middle attack)! It is also possible that a host key has just been changed. The fingerprint for the RSA key sent by the remote host is 51:82:00:1c:7e:6f:ac:ac:de:f1:53:08:1c:4d:55:68. Please contact your system administrator. Add correct host key in /Users/iodocsCalifornia/.ssh/known_hosts to get rid of this message. Offending RSA key in /Users/iodocsCalifornia/.ssh/known_hosts:12 RSA host key for 10.131.16.118 has changed and you have requested strict checking. Host key verification failed.
I had overwritten my previous key in my computer and used it with a new droplet (not the one I tried to connect when getting this message. That one actually asks for a password I have not received via e-mail)
Thinking that this message was probably related to that, I updated my SSH key in Azure with that new one from my computer again. But the message continued to show when trying to login in via ssh.
Awnser
Use ssh-keygen to delete the invalid key
ssh-keygen -R "you server hostname or ip"
Example:
By Windows Cygwin:
ssh-keygen -R "10.101.12.3"
Post reference ssh.com.
By linux:
ssh-keygen -f "/home/rck/.ssh/known_hosts" -R "localhost"
ssh-keygen Option Summary
Here is a summary of commonly used options to the keygen tool:
- -b “Bits”
This option specifies the number of bits in the key. The regulations that govern the use case for SSH may require a specific key length to be used. In general, 2048 bits is considered to be sufficient for RSA keys. - -e “Export”
This option allows reformatting of existing keys between the OpenSSH key file format and the format documented in RFC 4716, “SSH Public Key File Format”. - -p “Change the passphrase” This option allows changing the passphrase of a private key file with [-P old_passphrase] and [-N new_passphrase], [-f keyfile].
- -t “Type” This option specifies the type of key to be created. Commonly used values are: – rsa for RSA keys – dsa for DSA keys – ecdsa for elliptic curve DSA keys
- -i Input When ssh-keygen is required to access an existing key, this option designates the file.
- -f File Specifies name of the file in which to store the created key.
- -N New Provides a new passphrase for the key.
- -P Passphrase Provides the (old) passphrase when reading a key.
- -c Comment Changes the comment for a keyfile.
- -p Change the passphrase of a private key file.
- -q Silence ssh-keygen.
- -v Verbose mode.
- -l Fingerprint Print the fingerprint of the specified public key.
- -B Bubble babble Shows a bubble babble (Tectia format) fingerprint of a keyfile.
- -F Search for a specified hostname in a known_hosts file.
- -R Remove all keys belonging to a hostname from a known_hosts file.
- -y Read a private OpenSSH format file and print an OpenSSH public key to stdout.