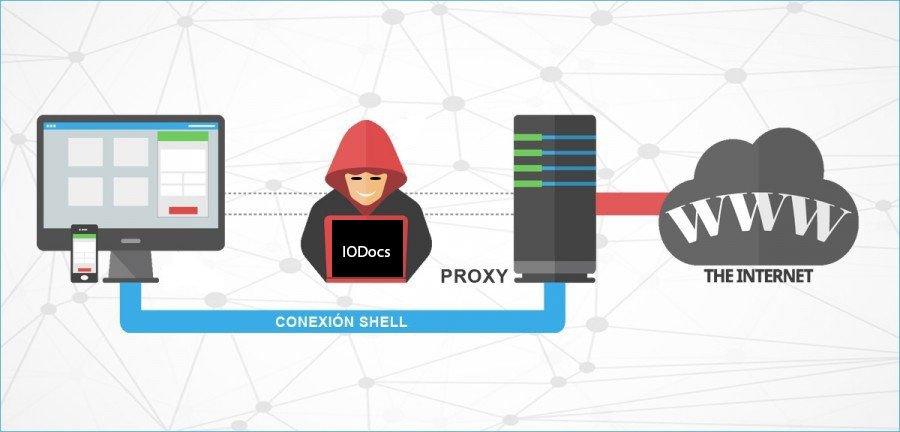
Configure Proxy Clients in Linux
Configure proxy settings like follows on Debian / Ubuntu Client
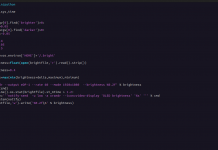
root@client:~# vi /etc/profile # add follows to the end (set proxy settings to the environment variables) MY_PROXY_URL="http://prox.srv.world:3128/" HTTP_PROXY=$MY_PROXY_URL HTTPS_PROXY=$MY_PROXY_URL FTP_PROXY=$MY_PROXY_URL http_proxy=$MY_PROXY_URL https_proxy=$MY_PROXY_URL ftp_proxy=$MY_PROXY_URL export HTTP_PROXY HTTPS_PROXY FTP_PROXY http_proxy https_proxy ftp_proxy root@client:~# source /etc/profile # it's OK all, but it's possible to set proxy settings for each application like follows # for apt root@client:~# vi /etc/apt/apt.conf # create new Acquire::http::proxy "http://prox.srv.world:3128/"; Acquire::https::proxy "https://prox.srv.world:3128/"; Acquire::ftp::proxy "ftp://prox.srv.world:3128/"; # for wget root@client:~# vi /etc/wgetrc # add to the end http_proxy = http://prox.srv.world:3128/ https_proxy = http://prox.srv.world:3128/ ftp_proxy = http://prox.srv.world:3128/
Advantages
In general, not just in computing, proxies make it possible to:
Control: Only the broker does the actual work, so you can limit and restrict the rights of users, and give permissions only to the proxy.
Savings: Only one user (the proxy) has to be prepared to do the actual work. By being prepared, we mean that it only needs the resources necessary to make that functionality. Examples of resources required to do the function can be computed capacity and logic or external network (IP) address.
Speed: If multiple clients are going to request the same resource, the proxy can cache: save a request’s response to give direction when requested by another user. So you don’t have to contact the destination again, and it ends faster.
Filtering: The proxy may refuse to respond to some requests if it detects that they are prohibited.
Modification: As an intermediary, it is, a proxy can falsify information, or modify it using an algorithm.
Inconvenience
In general, using an intermediary can cause:
Anonymity: If all users identify themselves as one, it is difficult for the accessed resource to differentiate them. But this can be bad, for example when identification needs to be done.
Abuse: Being willing to receive requests from and respond to many users, you may do some work that you don’t touch. Therefore, you have to control who has access and who does not have access to your services, which is usually very difficult.
Load: A proxy has to do the work of many users.
Intrusion: This is one more step between source and destination, and some users may not want to go through the proxy. Not least if it caches and saves copies of the data.
Inconsistency: If you cache, you might be wrong and give an old response when there is a newer one on the target resource. This issue does not exist proxy servers because they connect to the remote server to verify that the cached version remains the same as the version on the remote server.
Irregularity: The fact that the proxy represents more than one user causes problems in many scenarios, namely those that presuppose direct communication between 1 sender and 1 receiver (such as TCP/IP).